Currently, almost everyone performs their day-to-day functions through some sort of technology, whether it’s email, texts or even phone calls. Unfortunately, as the world becomes more and more digitally connected, the way people try to commit crimes has evolved. The days of thieves stealing the wallet out of your pocket aren’t over, but criminals of this variety have evolved into larger-scale theft of money and data through cyberattacks and scams.
In some of these cyberattacks, the perpetrator might send a message demanding a ransom in exchange for the return of your stolen data. The criminal may even make the data on your computer unreadable, or irrecoverable, until that ransom is paid—much like these two examples.
Colonial Pipeline – In 2021, the criminal group “DarkSide” breached Colonial Pipeline’s systems and shut down a major fuel supply system for the East Coast. Eventually Colonial Pipeline’s CEO authorized a ransom payment of $4.4 million to restore the systems. This was a very concerning attack as it affected a large fuel pipeline system for the East Coast and revealed vulnerabilities within the nation’s infrastructure when it comes to cyberthreats. It also caused panic amongst those affected by long lines and rising prices at the gas stations that had fuel.
JBS USA – In 2021, the criminal group “REvil” breached the systems of JBS during a Memorial Day attack. JBS is the world’s largest meat supplier, and this attack caused all their meat plants in the United States to be closed while work was performed to restore the systems. Ultimately JBS made the decision to pay the ransom of $11 million to restore their systems. This attack reminded everyone that the hacking groups of the world are always out there, even on holidays.
In attacks such as these, the goal of the affected companies is to restore systems as quickly as possible. In both of these high-profile instances, the quickest way to do so was to pay the ransom demands.
How attacks like these occur: Email phishing
Over 90% of successful data breaches start with a spear phishing email. Cybercriminals send email attachments or messages with links to viruses, allowing them to install malware or ransomware on your computer or your company’s network if you click on or open these items.
They may also gather information from your email address book to target more potential victims. They can sell this and any other data from your computer to other criminals, and that information can be used to cause problems for you, your company or even your clients. The best way to protect yourself, your business and Long & Foster is to think before you click or open any attachment you’re not expected.
Below are a few things to look for that can indicate if an email is legitimate or not.
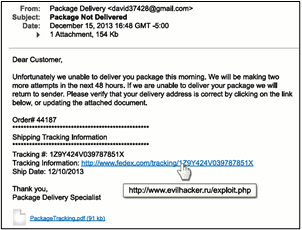
| Check the email address from which it is sent. If the email appears to come from a legitimate organization, but the “From” address is someone’s personal account, such as @gmail.com or @hotmail.com, this is most likely an attack. Also, check the “To” and “CC” fields. Is the email being sent to people you do not know or work with? If so, that should raise red flags. |
| Be suspicious of emails addressed to “Dear Customer” or that use generic salutations. If a trusted organization needs to contact you, they should know your name and personal information. Also ask yourself, am I expecting an email from this company? |
| Watch for grammar or spelling mistakes. Most businesses and professionals proofread their messages carefully before sending them. |
| Be wary of emails that require “immediate action” or create a sense of urgency. This is a common technique to rush people into making a mistake. Also, legitimate organizations will not ask you for your personal information. |
| Think before you click, and only click on those that you are expecting. Also, hover your mouse over the link to see the true destination of any hyperlinks. If the true destination is different than what is shown in the email, this is an indication of an attack. |
| Be suspicious of attachments. Only open those attachments you are expecting. Working Together to Protect You and Our Company In addition to your efforts to stay protected online and avoid phishing attempts, Long & Foster has systems in place to monitor and filter all incoming email messages. Currently, we block close to 40% of messages to come into our company, which accounts for an average of 90 million messages per year that are not legitimate. Even though these tools are in place, the hackers are constantly trying to gain access. That’s why it’s essential for you to play your part in our overall efforts to defend the company, our businesses and our customers from the bad guys. Questions about spam and cybercrimes? The Service Desk is available to assist at ServiceDesk@longandfoster.com |
